Smart Tips About How To Detect Conficker With Nmap
Published on january 2017 | categories:
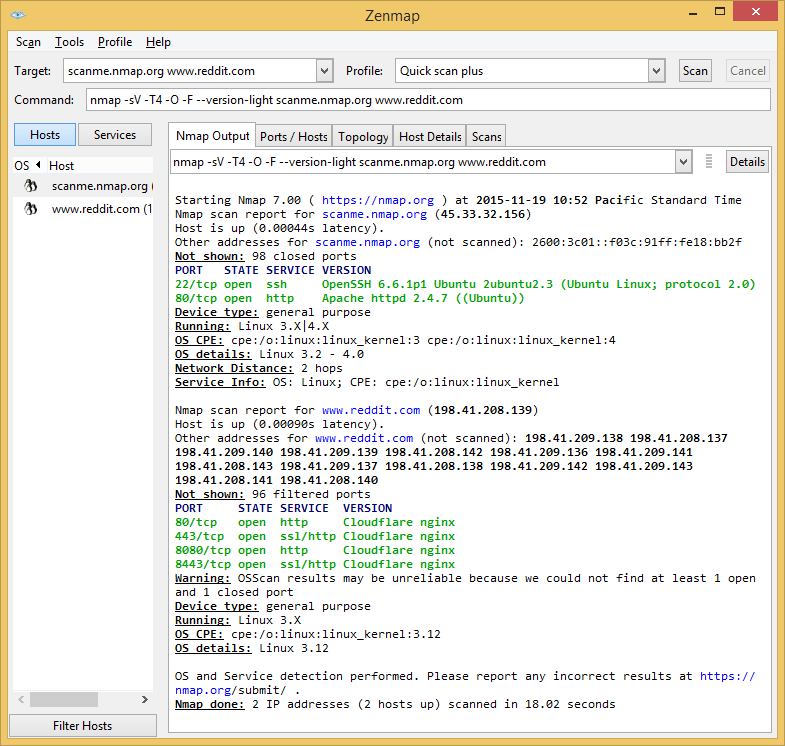
How to detect conficker with nmap. Nmap.org npcap.com seclists.org sectools.org insecure.org download reference guide book docs. Use a source rpm 2. Using nmap to scan for the famous conficker worm.
The scs tool wasn't very fast, although i did find that by performing an nmap of the network first to find hosts listening on port 445/tcp and feeding that list to scs, the scan. March 30, 2009 | 1 min read nessus plugin # 36036 performs a network based check for windows computers infected with a variant of the conficker virus. Compile straight from source, from the svn
Scanning for conficker with nmap 1. You can find it on the download page: Use nmap to locate infected machines.
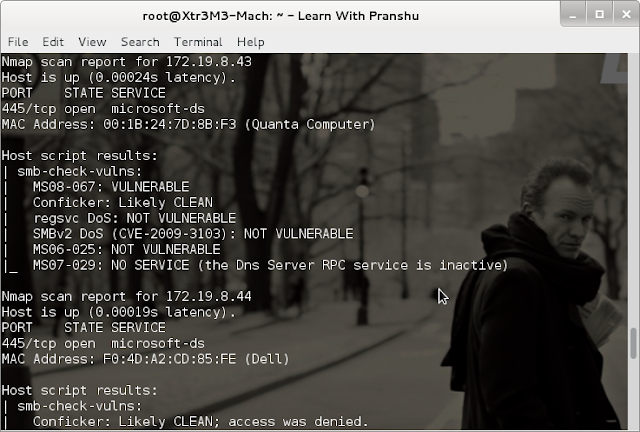
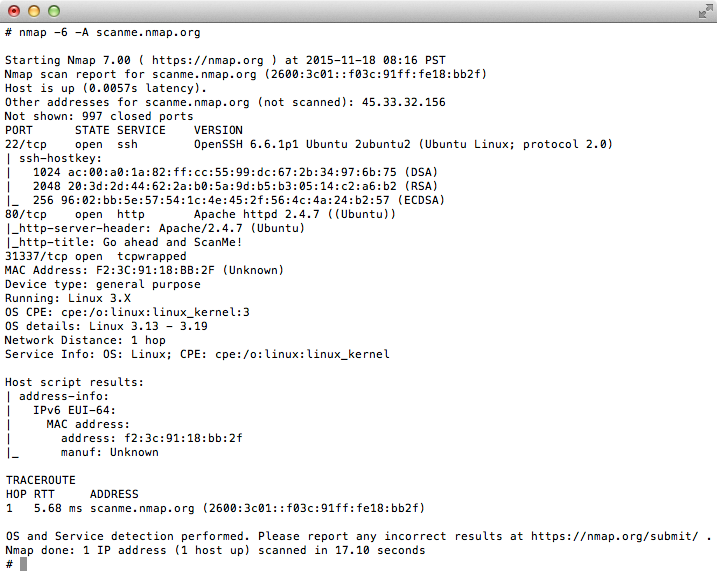
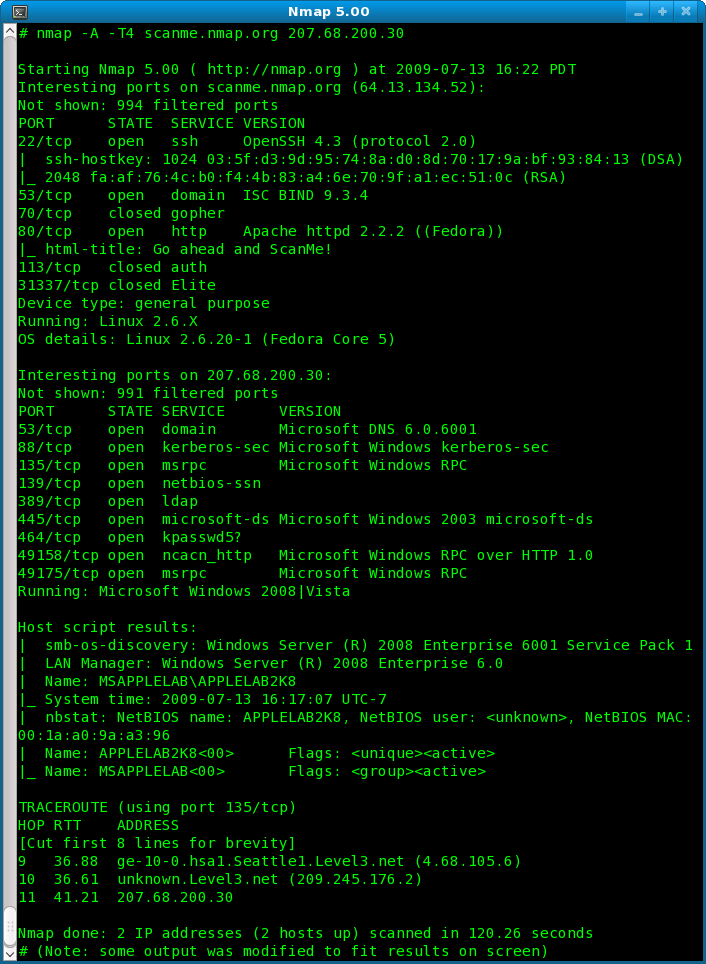
To scan for conficker, use a command such as: There are three options in the above command to help cut down on the amount of work nmap has to do per host: I figure everyone is good and ready for tomorrow but just in case you want to double check or still need to scan your network here is a quick and easy method with nmap.
Start the logging within wireshark. Detecting conficker worm with nmap. Ran nmap against our vlans on the impacted site with the following command:
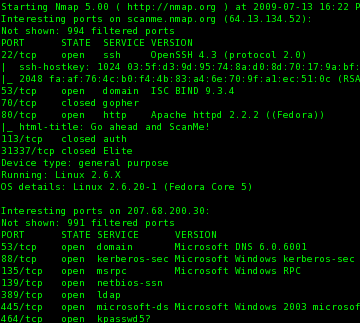
If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.
![Nmap Evade Firewall And Scripting [Updated 2019] - Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi1.jpg)



![The Nmap Command You Can Use Scan For The Conficker Virus On Your Lan: Nmap -Pn -T4 -P139,445 -N -V --Script=Smb-Check-Vulns --Script-Args Safe=1 [Targetnetworks] : R/Technology](http://blogs.developpeur.org/blogs/nicoboo/WindowsLiveWriter/FunNoslangagesdeprogrammationdanslesfilm_E585/fun_nmap_matrix_2.jpg)
![Nmap Evade Firewall And Scripting [Updated 2019] - Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi3.jpg)